Overview
Like previous technologies, such as the Internet, blockchains have been driven by a high degree of techno-optimism not yet backed up by on the ground impact or reliable evidence. Undoubtedly, the technology, which is still rapidly evolving, has enormous potential in many sectors and could promote human development if harnessed strategically. 
One of the many blockchain innovative traits is the use of sophisticated cryptographic tools to generate unique identities for individuals interacting within the distributed network. In principle, such identities can be pseudo-anonymous, immutable, secure and directly created and managed by their owners, thus not needing centralized or federated intermediaries. This, in principle, make blockchains an ideal candidate to propel further innovation in the digital identity sector. At this point, the critical question is how.
Taking a bird’s eye view of the sector, identity access and management face two significant challenges.
-
- Inclusion. Nowadays, one out of seven people in the world has no legal identity. Similarly, one out of every three children is not registered at birth. Refugees who have “lost” their identity while migrating could also be added here. While declining in recent years, these numbers are still staggering, particularly for the so-called digital age. This is the critical issue that initiatives such as ID for Development and ID2020 are trying to address.
- Ownership and management of personal identity. Traditional centralized models typical of most of the 20th century implicitly by-passed the issue as third parties, public or private, were entirely in charge of the process. Individuals were content with receiving various pieces of identity that they managed to make claims and obtain products and services. The advent of digital identity allowed private companies to commoditize identity and make it part and parcel of new business models unthinkable last century.
Individuals now give away identity attributes in exchange for free online services. Users have little to no control of their own identities. Identity ownership seems to be in the hands of third parties. In fact, a large market for buying and selling identity information has emerged in the last 10 to 15 years. Identity owners have no saying on this, nor do they directly benefit from any of these transactions.
While blockchain technology seems to be well suited to address the second of these core issues, their relevance for the first remains to be explored in more detail. Certainly, self-sovereign identity (SSI) and similar alternatives offer great potential to users willing to take control of their own digital identities. However, given the complexity of the technology, relatively high entry barriers, and overall usability challenges, blockchains might not be the first option for fostering identity inclusion.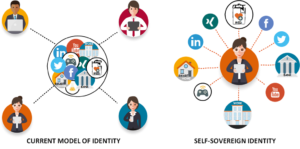
Factoring into the ID equation, the distinction between public and private goods (and services) further elucidates the issues’ multi-dimensional character. Lack of legal ID usually translates into a lack of access to public goods by unidentified populations. On the other hand, private goods such as banking and financial services are more prone to benefit from a technology that has financial incentives built-in. That is certainly not the case with public goods.
At the moment, several blockchain-based initiatives using SSI are already delivering on the ground, working independently from legacy platforms, including digital ones. On the other hand, very few governments are exploring the potential of BCT to deliver legal ID.
Identity access and management overview
Modern identity and access management (IAM) have been around since the late 1930s when European countries issued national ID cards. More recently, IAM has benefited from biometrics and the emergence of digital platforms and solutions. Digital identity is indeed becoming the default standard for most if not all forms of ID. Recent estimates suggest that over one hundred countries currently issue national ID cards of various sorts.
Having substantially evolved in the last 60 years or so, IAM has also accumulated a substantial body of knowledge and experience that cannot be summarily dismissed in the name of technological disruption or radical innovation. On the contrary, new technologies such as blockchains could, in fact, have maximum impact if they can effectively tackle the core issues and gaps IAM currently faces. Privacy, ownership, security, and transparency are a few of the themes that new technologies could address innovatively.
Four pillars are used to characterize IAM’s core functions. They are:
- Administration, including standards setting, attribute collection and storage, access, and service provision.
- Authentication links users to attributes collected.
- Authorization provides access to goods and services (including information) based on attributes.
- Auditing or monitoring user access to resources. Also entails creating governance mechanisms that address ownership, privacy, security, transparency, and accountability issues and establishes auditing policies and rules.
The four IAM pillars are closely interconnected. Ongoing IAM decentralization trends such as federated platforms, user-centric, and even emerging distributed systems do not necessarily change this structure. But they do alter how each of them is designed and implemented on the ground.
From the end-user perspective, identity envisages three different elements. The first is proof of identity. The second is attestation of identity by a third party. And finally, claims that users are entitled, based on either of the previous two. Proof and attestation demand the collection and storage of a person’s attributes based on some sort of standards. To make a claim, individuals must provide proof of identity (or be authenticated in digital platforms) and, at the same time, be authorized to make such a claim and obtain the product or service sought.
Two generic types of identity are used to describe IAM. The first one is foundational identity, which is usually equated with a legal identity. Here, after collecting attributes, individuals are issued a unique ID that is legally recognized at the national level and could be used to access a wide variety of services. Legal IDs are almost always issued by the state in a centralized fashion. National ID cards are perhaps the best example of a foundational identity.
The second type is called functional or transactional ID. In this case, a particular entity, public or private, issues individuals or customers a unique ID that is only valid for the specific purposes previously established by the issuing body. Electoral databases or registries are a good example here. On the private sector side, M-Pesa in Kenya uses mobile phones to provide financial identity to customers with no access to banking services. Functional IDs are, for the most part, also issued in a centralized fashion. However, the area has been evolving in the last ten years to a more decentralized and user-centric model, led by the private sector.