The Evolution of Digital identity
The emergence of digital technologies provided the ground to shift from traditional systems based on physical identity. In the past, both foundational and functional identity mechanisms were centralized, with individuals getting a physical document containing relevant personal attributes required by the issuing entity. Document management was totally in the hands of the end-user, who used them as proof of identity to make claims in person.
The Internet and the digitalization of biometrics and other personal attributes propelled new ways of issuing and managing personal identity. This process started around the end of the last century and allowed Internet companies to start giving their users online identities. It also promoted efforts to release functional identities that could be used across different interconnected networks, thus opening the door for potential decentralization.
The evolution of digital identity is summarized in table 1, highlighting the evolving nature of IAM from a centralized model to a potentially fully distributed one.
Table 1: Digital Identity Evolution
| Digital Identity | |
| Centralized | Single provider or hierarchy of providers
|
| Decentralized |
Federated
User-Centric
|
| Distributed | Self-sovereign identity (SSI)
|
Distributed ID is one of the emerging areas in the field and one where BCT could impact. Distributed ID is closely related to the concept of SSI, which is not limited to BCT but rather covers the whole DLT domain.
Identity access: Inclusion via ID for Development
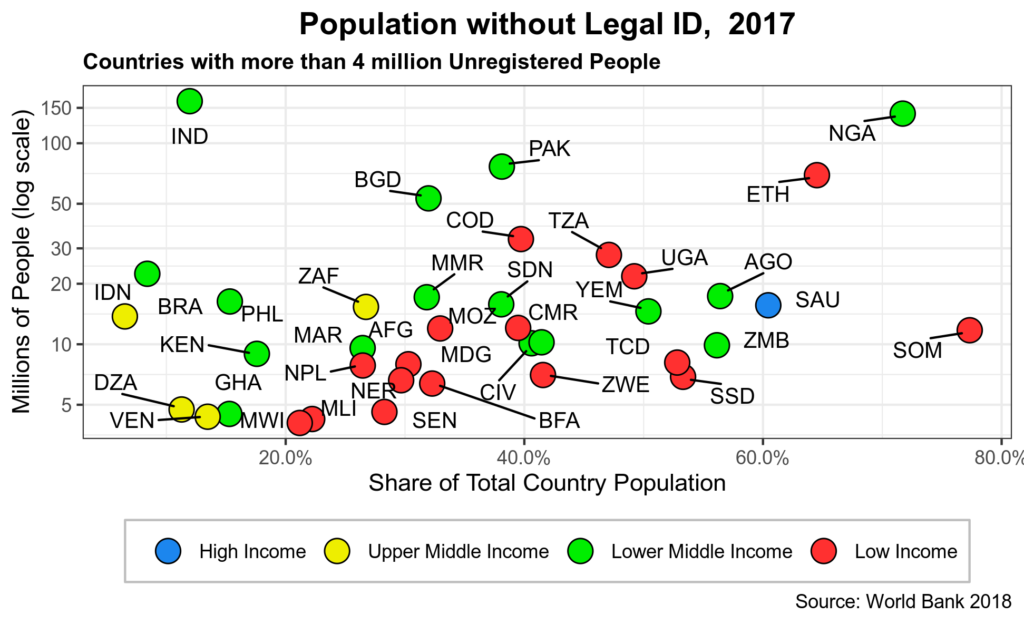
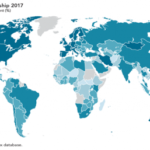
While IAM has substantially evolved in the last fifty years, over one billion people in the world currently have no legal identity, according to the World Bank’s latest estimates. As shown in figure 1 below, this gap affects most countries regardless of national income levels. However, poorer countries report a higher number of people with no legal ID, including children under five who are never registered. The UN Sustainable Development Goals (SDGs) explicitly address the latter through goal 16.9.
Figure 1: Population with no Legal
The figure also shows that at least 60 percent of the population of Nigeria, Saudi Arabia, Somalia, and Ethiopia lack legal ID. India, Nigeria, Pakistan, and Ethiopia have at least 50 million inhabitants who are not registered. Spain seems to be lagging in the developed world as close to 25% of its population has no legal ID. In any event, such gaps should be kept in mind when planning and designing new solutions using new technologies to close the ID global gap.
ID4D bets big on digital identity, highlighting the potential that new information and communications technologies (ICTs) such as the Internet, cloud computing, smart cards, and mobiles can play in the process. This is not without risks, as digital divide components and complexities will come into play here.
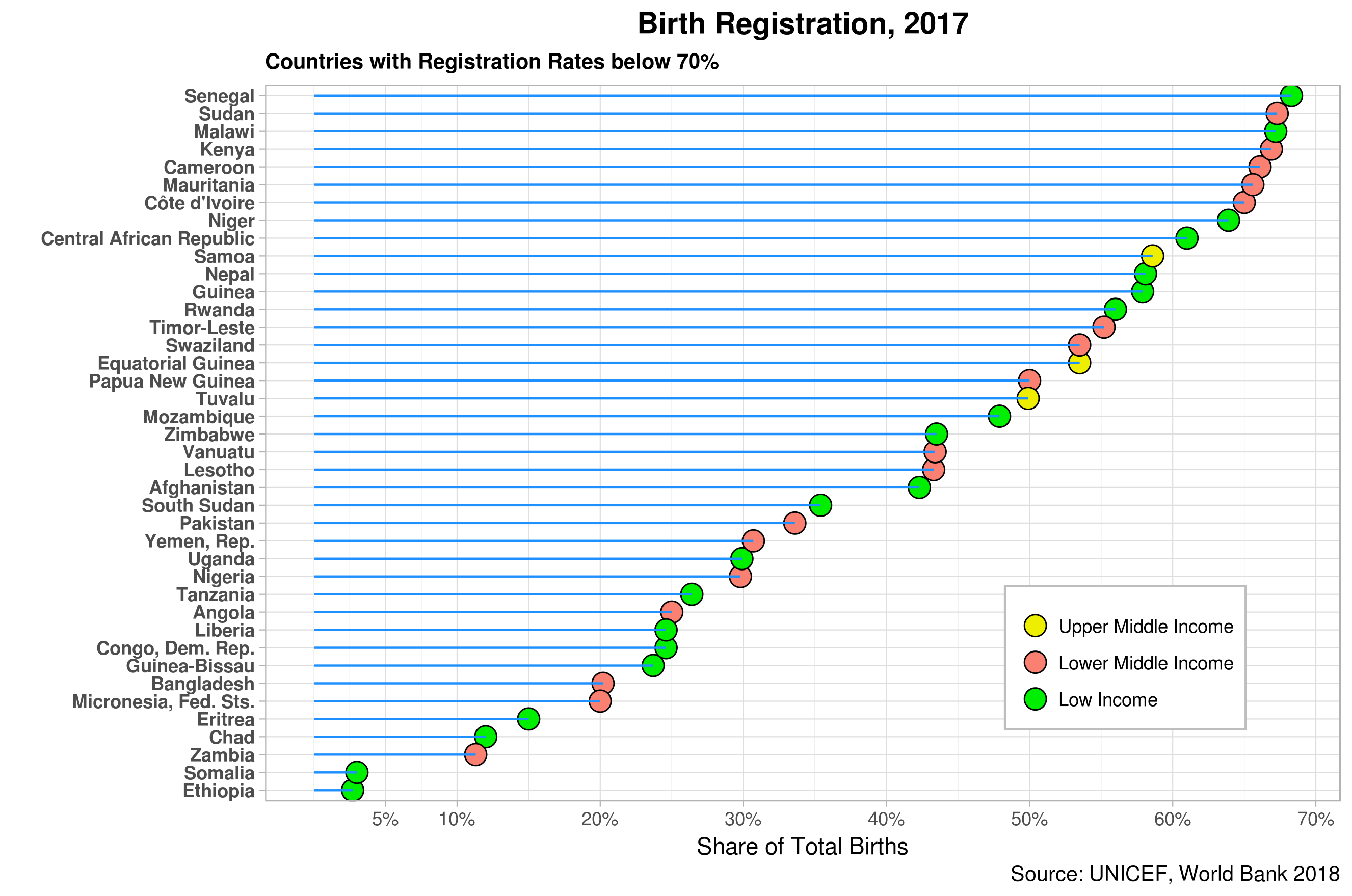
Figure 2 shows the latest data available for birth registration by country. As expected, most countries lagging in this area are in the low-income brackets but limited to Africa and Asia.
Figure 2: Birth Registration
A consortium of public and private organizations led by the World Bank has agreed on ten ID principles in sustainable development. The principles are summarized in the table below.
Table 2: ID4D Principles
| Inclusion | Design | Governance |
| Universal coverage | Robustness | Preserves rights, privacy, and security |
| Digital divide reduction | Interoperable and responsive | Institutionalization and accountability |
| Open standards, technological neutrality | Independent oversight, redress mechanisms | |
| Proportional data collection, minimal disclosure | ||
| Financial and operational sustainability |
Note that at least two of the principles are directly linked to new ICTs, namely, reducing the digital divide and using open standards. In turn, most others could undoubtedly be enhanced in both design and implementation of new technologies are factored in from the very start.
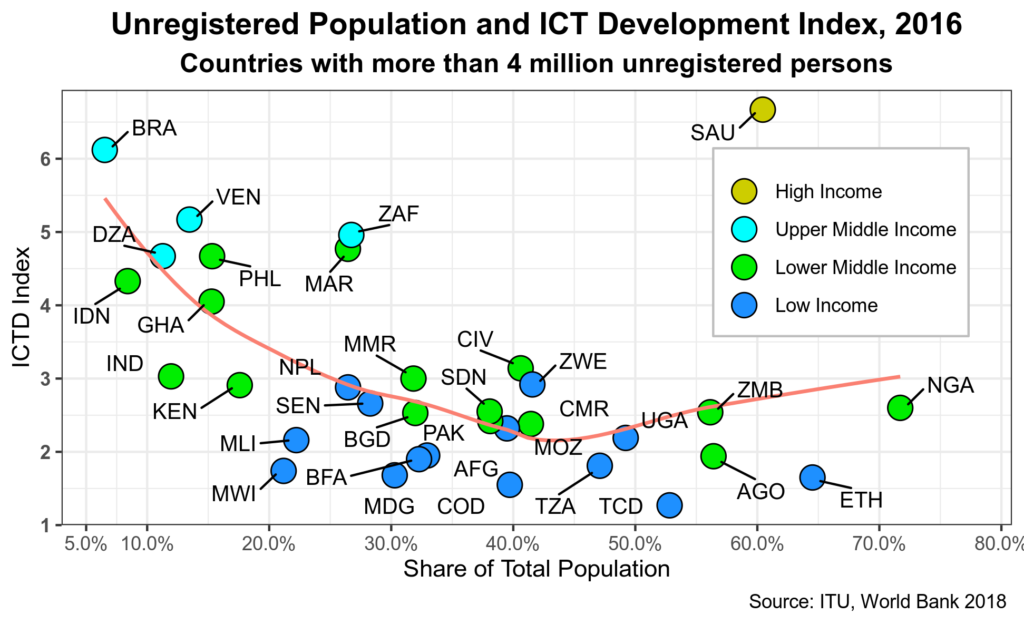
Figure 3 shows the relation between unregistered populations and the ICT Development Index created by the ITU.
Figure 3: Unregistered Population and ICT
While there seems to be some correlation between people without legal ID and ICT, lower-middle and low-income countries seem to have similar levels of ICT but a wide range of unregistered population levels. And in some cases, higher ICT levels go hand in hand with higher numbers of unregistered people.
ID4D is agnostic about the character of an IAM network. That is, the principles should hold in any network setup, from centralized to distributed.
Identity management: Ownership via Self-Sovereign Identity
The evolution of digital identity shows a trend towards decentralization combined with efforts to empower identity owners and put them entirely in charge of both access and management of their own identities. Federated and user-centric approaches have fallen short of this latter goal. Here, BCT could make a big difference, although not necessarily using a distributed system, particularly for foundational identity.
The best example of a distributed IAM system is SSI. SII is openly promoted by the BCT and DLT communities and, in fact, is currently being deployed by a few startups, mostly in the developed world. In this scenario, the user is in full control of its own identity attributes and has a saying on dissemination and governance mechanisms to run the overall ID process.
The way individuals control their identity in SSI systems is simple: they directly “collect” identity attributes themselves and store them on a digital identity wallet that is under their control and permanent supervision. Cryptographic tools play a key role in creating a unique universal ID based on public-key cryptography. Proofs, attestations, and claims can then be added to such a unique identity, which is pseudo-anonymous and added to the individual’s digital identity wallet in question.
Note that the blockchain or distributed ledger is not used to store such information. What is recorded are the events that one person has been part of and which have demanded the use of its unique digital identity – a public key that is validated by the user’s own private key.
Coincidentally, the SII community has also identified ten principles, presented in table 3.
Table 3: SSI Principles
| Governance | Design | Security |
| Existence | Interoperability | Persistence |
| Control | Portability | Protection |
| Access | Minimization | Transparency |
| Consent |
SSI focuses on the individual who should have full identity ownership and manages it accordingly. Not surprisingly, the key SSI categories are related to the overall governance of personal identities. The individual is in complete control and does not depend on others to do so.
Overall Approach
All of the above provide sufficient material to build a framework that explores how BCT could play a role in addressing the core issues faced by IAM.
First, the four IAM pillars for digital should serve as the overall basis for such a framework. Having carefully looked at current identity access and ownership gaps, it is clear that governance processes and mechanisms do not seem to have the required importance within IAM. However, addressing this should not be complicated as governance is subtly subsumed under the audit component. The suggestion here is to reverse this logic and make governance the relevant pillar.
As a result of this change, the sequencing of the pillars needs to be revisited. From a design perspective, the governance pillar should be the starting point for any IAM initiative or project. The governance approach defined from the very start of the effort and the mechanisms established to make it work will determine how administration, authentication, and authorization are designed and deployed. Recall that governance issues are part of the principles of both ID4D and SSI.
The distinction between foundational and transactional ID is also critical. Note that these categories are not immutable, a la BCT. On the contrary, foundational ID can also act as transactional. On the other hand, functional or transactional ID has served as a catalyst to create foundational systems. Electoral databases in developing and emerging economies are the best examples here. In some industrialized countries, driver’s licenses are used as the primary form of legal ID.
Introducing at this point, the distinction between public and private goods helps reinforce the above difference. In principle, foundational ID systems should be the basis for providing all public goods, services, and information. However, this is not the case in many countries, including developed nations. Estonia is perhaps the best example of a foundational system used for most transactions, both public and private. Note that aspirationally at least, SII has precisely the same goal. At this point, many public goods and services are furnished via functional IDs. They seem to be operating at some optimal levels while filling the glaring gaps left by the lack of legal identities, especially in developing countries.
The last element of the framework is defined by the type of network envisaged by the ID systems. Centralized, decentralized, and distributed are alternatives. While this might be a critical component, arguing otherwise is also possible as long as the adopted governance principles and mechanisms are completed and implemented on an open and participatory basis. Similarly, distributed systems might not be the only ones that can guarantee that the ownership of a person’s identity is entirely in the individual hands. While broader in scope and objectives, the European General Data Protection Regulation is a step in this direction – albeit a small one in the overall context of the identity management problematic.